2023 has been a very eventful year for OSV.
New ecosystems support
OSV Schema adoption continues to grow! This year alone, 8 new ecosystems have adopted the schema, and are now included in our OSV.dev database:
- AlmaLinux
- Bitnami
- Curl (currently blocked on #1235 for ingestion into OSV.dev)
- Malicious Packages
- R
- Rocky Linux
- Haskell
- Python Software Foundation
This has brought the total number of supported ecosystems to 20. In particular, we have seen increased interest from Linux distributions, and expect to see further growth in adoption in 2024.
C/C++
C and C++ dependencies remain a critical pillar of open source supply chains. We’ve expanded our C and C++ coverage by enriching our database with over 30,000 advisories with commit-level vulnerability information sourced from NVD’s CVE records.
Our commit level vulnerability information paired with the experimental determineversion API enables OSV-Scanner to detect vulnerabilities in C and C++ dependencies used as submodules or directly vendored into source code. Our improvements in C and C++ support closes an important gap in vulnerability detection.
Infrastructure
Behind the scenes, we’ve optimized OSV.dev’s API for performance and reliability, to ensure we maintain our recently defined Service Level Objectives.
We’ve also made changes to make our API easier to use, such as returning the transitive closure of aliases to make it easier for users to deduplicate OSV entries across different databases.
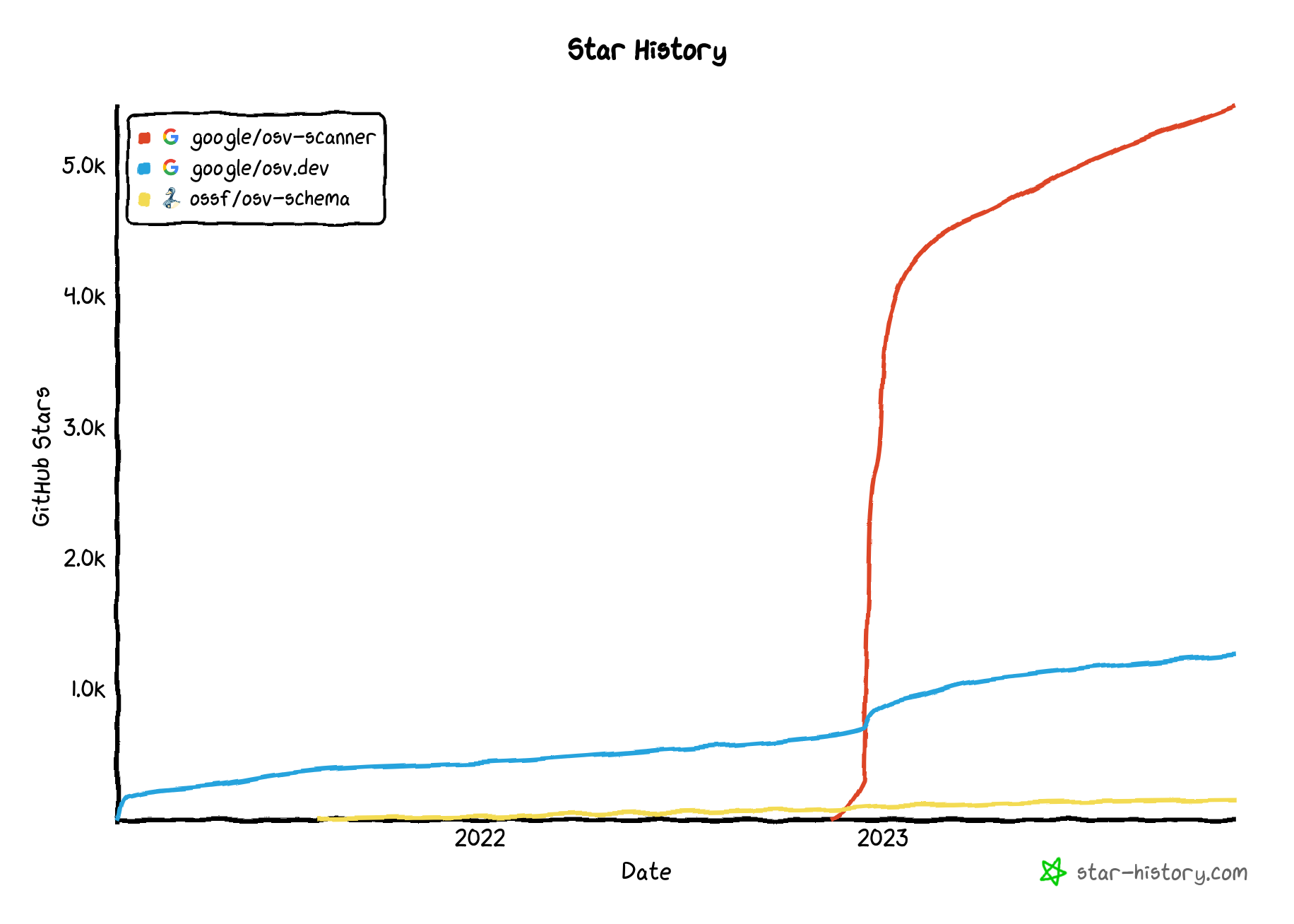
We saw peaks in API usage of over 300 QPS in November.
Community
There’s been a very pleasing uptick in both interest and external contributions to both OSV.dev (23 total contributors) and OSV-Scanner (32 total contributors)
We also gave an update on OSV at the OpenSSF Day Europe, in Bilbao, Spain in September.
Tooling
Since OSV-Scanner’s launch one year ago, we’ve added several significant new features.
- Reachability analysis to reduce false positives
- Govulncheck integration to enable reachability analysis of Go vulnerabilities
- Experimental Rust call analysis to enable reachability analysis of Rust vulnerabilities
- Comprehensive C/C++ vulnerability management support
- Git submodule scanning
- Vendored dependency detection
- Improved ecosystem and scanning format support
- Improved SBOM support
- NuGet
- ConanCenter
- An experimental offline mode
- An experimental GitHub Action (including SARIF output support)
- An experimental license scanning feature
More to come in 2024
The team is looking forward to much more to come in 2024 and the OSV Schema and OSV.dev’s third birthday in February, and OSV-Scanner’s first birthday in December.
We have a lot more exciting work planned in 2024, that we’ll share more details soon. Our main priorities for 2024 are centered around improving data quality and providing accurate and actionable results that lead to easy remediation.
We will support these priorities in the following ways:
1. Building validation and feedback mechanisms for OSV sources to ensure high data quality
As OSV Schema adoption grows, it’s become even more important to ensure consistency and high data quality across all data sources. We plan to provide better validation tools, and build feedback channels to make it easier for OSV data sources to ensure high quality of data.
2. Ensuring accurate and comprehensive scanning
A continuing focus for OSV-Scanner is making sure that our scanning is comprehensive and accurate. Accuracy is especially important for us, as one of our core goals is to minimize false positives and vulnerability noise for developers at the receiving end of the scanners.
3. Improving container scanning
OSV-Scanner has so far focused on source repository scanning. One important gap we aim to fill is to provide better support for container scanning, in a way that provides actionable and useful remediation guidance.
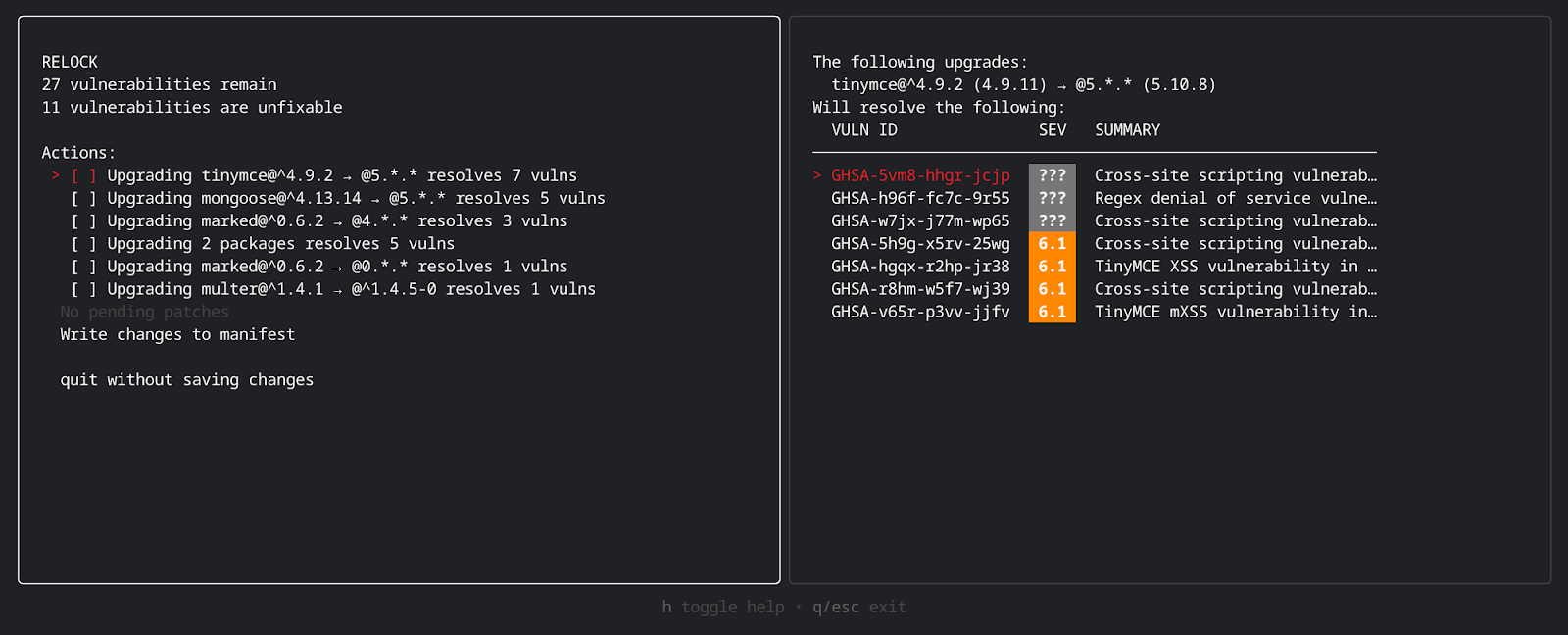
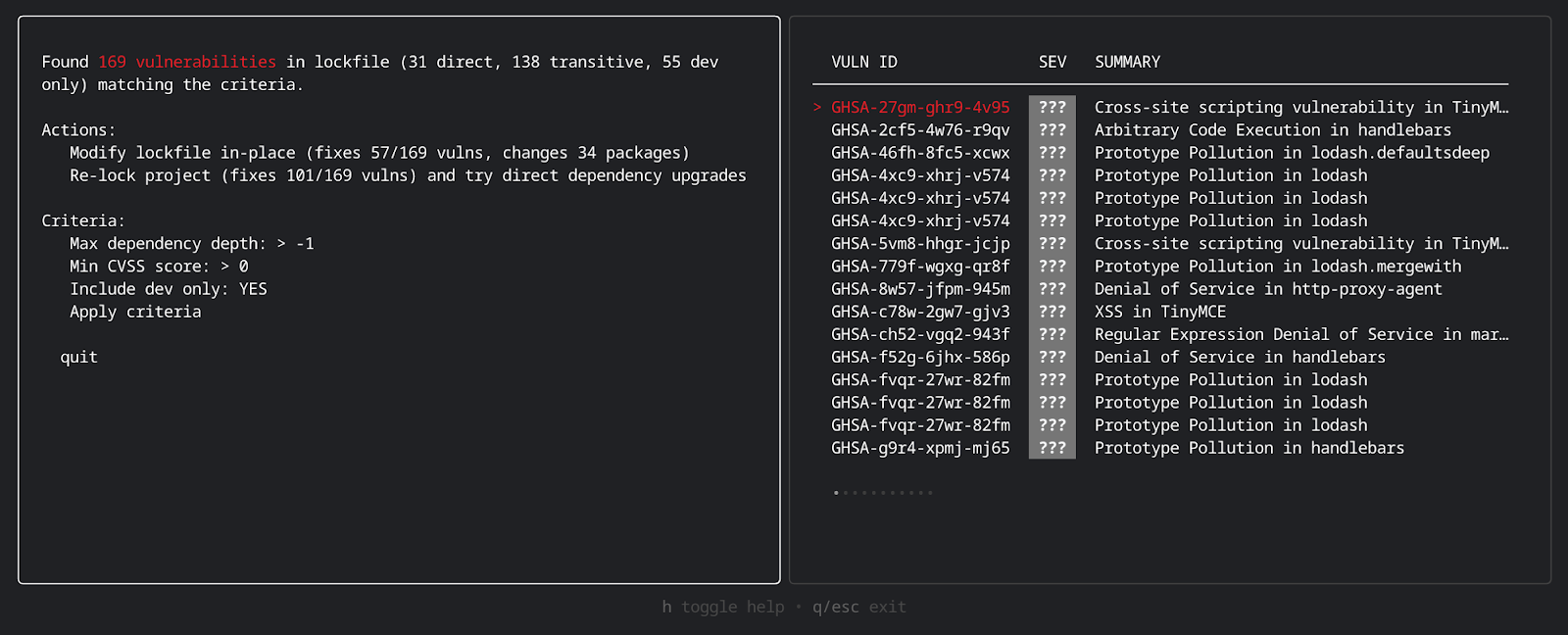
4. Releasing remediation tools
Developers are often faced with an overwhelming number of vulnerabilities reported against their dependencies. We are currently building tooling to enable developers to both interactively and automatically prioritize and fix the vulnerabilities that matter in an easy way.
Here’s a quick preview of what we have been working on: